Using Kerberos authentication
Whether Qlik Replicate Server is running on Linux or Windows, you can configure it to authenticate itself against the Hadoop cluster using Kerberos.
This requires you to perform the following steps on the Qlik Replicate machine before starting the Qlik Replicate Server.
Using Kerberos authentication on Linux
To use Kerberos authentication on Linux:
The commands described below should be issued under the "Attunity" user or under the user that was selected during the Replicate installation.
-
Obtain a valid TGT (Ticket-Granting Ticket) from the Kerberos KDC (Key Distribution Center) but save the TGT to a non-default cache file. Usually, a keytab file is used to perform non-interactive authentication to Kerberos.
Command Syntax:
kinit -kt [keytab_file] -c [cache_file_name] [principal_name] -
This step is only required for the global Kerberos ticket file. Set the Kerberos cache environment variable (for Replicate to use later on).
To set the environment variable:
-
Change the working directory to the Replicate "bin" directory by issuing the following command (assumes the default installation path):
cd /opt/attunity/replicate/bin -
Stop the Qlik Replicate Server services on the Linux by running:
/opt/attunity/replicate/bin/areplicate stop
-
-
Create a file named
site_arep_login.shin the Qlik Replicate bin folder.-
Add the following command to the file:
export KRB5CCNAME=cache_file_nameExample:
export KRB5CCNAME=/temp/kerberos/global.ticket
-
Save the file and
-
Start the Qlik Replicate Server services on the Linux by running:
/opt/attunity/replicate/bin/areplicate start
-
Now, whenever Qlik Replicate needs to use Kerberos authentication, it will perform the following operations:
- When Use global Kerberos ticket file is selected: Replicate will check whether the KRB5CCNAME environment variable is set and, if so, will use the ticket(s) inside the cache file specified by the environment variable.
-
When Use specific Kerberos ticket file is selected:
- During design-time (e.g. when selecting tables, testing the connection, etc.), Replicate will use the ticket(s) inside the cache file specified by the KRB5CCNAME environment variable.
- During runtime, Replicate will use the ticket file specified in the Hadoop endpoint settings.
Information noteIf the ticket in the cache file expires or becomes invalid, repeating the
kinitcommand shown in Step 1 above will write a new TGT to the cache file and allow Qlik Replicate to continue working. This can be done without restarting the Qlik Replicate Server.
Using Kerberos authentication on Windows
Before beginning, make sure that the impersonated user (principal) is granted read and write permissions on the Replicate Data directory (<product_dir>\Data by default) on the Qlik Replicate server. For Active Directory KDC, the impersonated user is the user configured in the user interface. For MIT KDC, this is the Windows user to which the MIT principal is mapped.
To set up Kerberos authentication on Windows, perform the following steps to ensure that the impersonated user (principal) has the Log on as a batch job privilege on the Qlik Replicate server.
-
On the Qlik Replicate Server machine, open the Local Security Settings (Control Panel > System Security > Administrative Tools > Local Security Policy).
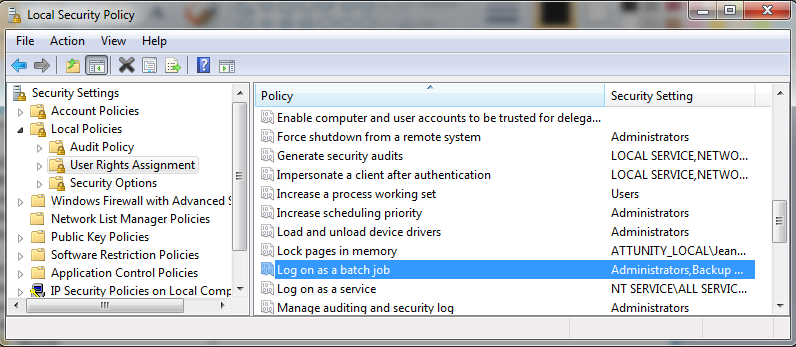
- In the console tree, expand Local Policies and select User Rights Assignments.
- In the details pane, double-click Log on as a batch job.
-
In the Log on as a batch job Properties dialog box, on the Local Security Settings tab, verify that the relevant user is listed. If the user is not listed, click Add User or Group, then add the user and click OK.
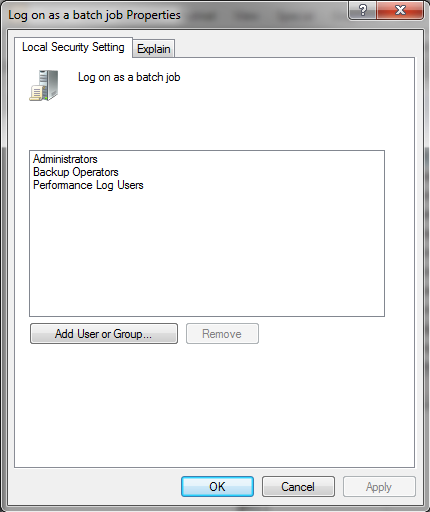
Your changes should take effect immediately.
MIT Kerberos
When MIT Kerberos is set in the endpoint, you need to perform the following steps to allow the Qlik Replicate server process to keep a specific privilege on startup. By default, Qlik Replicate server drops all privileges on startup. These steps are not required if you use Active Directory KDC.
- Open the Windows registry (regedit.exe).
-
Browse to: HKEY_LOCAL_MACHINE\SOFTWARE\Qlik\Qlik Replicate\Services\AttunityReplicateServer
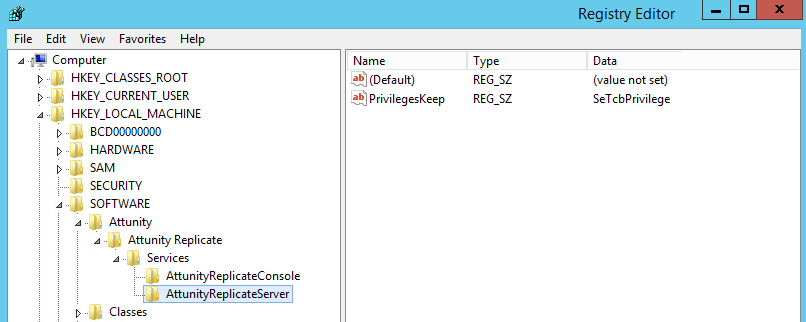
- Modify the
PrivilegesKeepstring to include the valueSeTcbPrivilege. - Close the Registry Editor window.
- Restart the Qlik Replicate Server service.
