Configuring tenant encryption
Set up tenant encryption in Qlik Cloud using your organization's AWS Key Management Service (KMS) keys.
Tenant admins can configure tenant encryption settings. By default, a new tenant uses the Qlik Internal KMS to encrypt content in the tenant. If your organization wants to use its own customer managed key (CMK) to encrypt tenant data, you can configure tenant encryption to use a CMK from a supported key provider.
Qlik Cloud supports using a CMK from the Amazon Web Services (AWS) Key Management Service (KMS). Customers can choose to use the same key for multiple tenants through the AWS KMS key policy definition, although this is not recommended as best practice. The CMK and AWS KMS integration will maintain per tenant encryption using the AWS KMS API's encryption context, but you must configure encryption for each tenant individually. Customers or partners enabling tenants for use by multiple end-user organizations are required to implement individual keys per end-user organization.
CMK prerequisites
You must have an AWS account and AWS KMS key to use CMK with Qlik Cloud. For more information about setting up an AWS KMS account and creating an AWS KMS key, see AWS Key Management Service (KMS).
After you have completed the setup in AWS, you can change the key provider in the tenant to use your AWS KMS key.
Create a new key provider in the tenant
Before you create the key provider, verify that your AWS KMS key and policy have been correctly configured in AWS KMS. See AWS Key Management Service (KMS). Qlik Cloud supports the following key providers:
-
Qlik Internal KMS (this is the default KMS using Qlik-managed keys)
-
AWS KMS
Do the following:
-
In the Administration activity center, go to the Settings page, then select the Tenant tab.
-
In the Tenant encryption section, click Manage key provider.
-
Click the Create new card.
-
Enter the parameters required by the key provider.
- Master key provider: The AWS KMS master key provider is the only option available.
- KMS key ARN: The KMS key ARN or the alias ARN. The key ARN is the Amazon Resource Name (ARN) for a KMS key. The alias ARN is the Amazon Resource Name (ARN) of the AWS KMS alias (the friendly name given for the AWS KMS key when the key was created). For more information, see Key provider events For information about how to find the key ARN or alias ARN of a KMS key, see Finding the key ID and key ARN or Finding the alias name and alias ARN.
- Title: A title to identify the new key provider.
- Description: Optional
Create key provider card
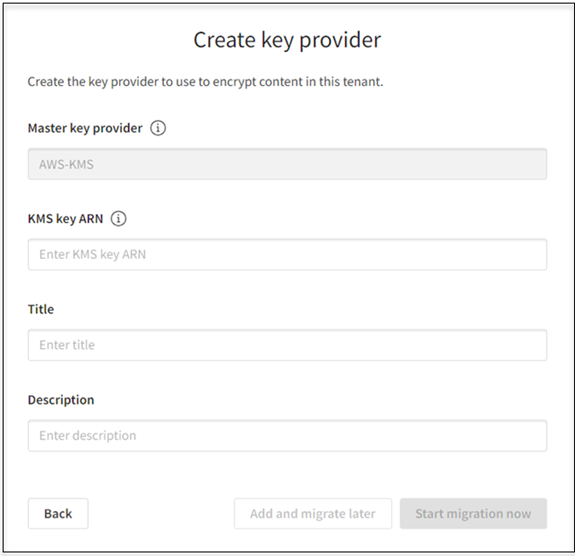
-
Choose whether you want to add the key provider configuration and save it for later use or start the key migration now.
Change the key provider in the tenant
You can change the key provider from Qlik KMS to AWS KMS, AWS KMS to another AWS KMS, or revert to Qlik KMS from AWS KMS. During the key migration process, the tenant will continue to function as usual with no impact to users.
Do the following:
-
In the Administration activity center, go to the Settings page, then select the Tenant tab.
-
In the Tenant encryption section, click Manage key provider.
- Click
on the card of the key provider that you want to migrate to.
- Select Migrate.
- In the Change key provider dialog, select the checkbox to confirm replacement of the current key and click Change key provider. Upon successful migration, the migrated key provider will become active.
Validate the key provider
At any time, you can validate an AWS key provider. Validation completes all the sanity checks and verifies adherence to defined rules required for the key provider migration. Validation is also performed automatically before the start of any key provider migration.
Do the following:
-
In the Administration activity center, go to the Settings page, then select the Tenant tab.
-
In the Tenant encryption section, click Manage key provider.
- Click
on the key provider card.
- Select Validate.
Delete a key provider
Any key provider, with the exception of the default Qlik key provider, can be deleted if it is inactive.
Do the following:
-
In the Administration activity center, go to the Settings page, then select the Tenant tab.
-
In the Tenant encryption section, click Manage key provider.
- Click
on the key provider card.
- Select Delete.
Key provider events
You can verify changes to the encryption key provider on the Events page in the Administration activity center. The events log captures the following encryption event types:
- com.qlik.v1.encryption.keyprovider.created
- com.qlik.v1.encryption.keyprovider.updated
- com.qlik.v1.encryption.keyprovider.deleted
- com.qlik.v1.encryption.keyprovider-migration.triggered
- com.qlik.v1.encryption.keyprovider-migration.finished
- com.qlik.v1.encryption.keyprovider-migration.progressed
Events in AWS KMS are logged to AWS CloudTrail under Event History. Search for the Event Names: Encrypt, GenerateDatakey, or Decrypt.
Qlik encryption API and connectors
In addition to configuring tenant encryption through the Administration activity center, Qlik offers several more ways to manage key provider lifecycles.
- An encryption API to manage the key providers programmatically. See API reference documentation at qlik.dev.
- An AWS KMS Qlik Automate Connector that enables you to configure the key providers in AWS . See How to get started with the Amazon KMS connector.
- Qlik Platform Operations Connector and QCS Connector, which are available as a no-code, Qlik-native option to easily manage key providers by manipulating connector blocks in a logical flow. See Qlik Platform Operations connector overview and Qlik Automate connectors.
AWS Key Management Service (KMS)
Qlik Cloud supports using a customer managed key (CMK)—Amazon refers to this as an AWS KMS key or KMS key—from AWS KMS to encrypt and decrypt your tenant data.
Below are the general steps required to set up AWS to use with CMK. You must create an AWS KMS account, create your AWS KMS key, and configure your key policy for use with Qlik Cloud CMK. After you have completed the setup in AWS KMS, you can change the key provider in your Qlik Cloud tenant to use an AWS KMS key. See Create a new key provider in the tenant.
Create an AWS account
Go to Amazon Web Services and create an account.
Create a symmetric AWS KMS key
In AWS, create a key using the AWS KMS Management Console or through the AWS KMS API using the CreateKey command. When configuring your multi-region key, keep in mind that there are limitations to which regions can be selected as backup regions depending on the primary key's region.
-
AWS Region—Select the region where your Qlik Cloud tenant is hosted. Supported Qlik Cloud regions and their associated AWS backup region codes are listed below. Multi-region keys are supported.
Primary region name Primary region code Backup region name Backup region code US East (North Virginia) us-east-1 US East (Ohio) us-east-2 Europe (Ireland) eu-west-1 Europe (Spain) eu-south-2 Europe (London) eu-west-2 Europe (Spain) eu-south-2 Europe (Frankfurt) eu-central-1 Europe (Milan) eu-south-1 Europe (Sweden) eu-north-1 N/A N/A Asia-Pacific (Singapore) ap-southeast-1 Asia Pacific (Seoul) ap-northeast-2 Asia-Pacific (Sydney) ap-southeast-2 Asia Pacific (Melbourne) ap-southeast-4 Japan (Tokyo) ap-northeast-1 Japan (Osaka) ap-northeast-3 India (Mumbai) ap-south-1 India (Hyderabad) ap-south-2 Middle East (UAE) me-central-1 N/A N/A Israel il-central-1 N/A N/A Brazil (BR) sa-east-1 N/A N/A France (FR) eu-west-3 N/A N/A The eu-north-1 Sweden region does not have a backup region due to its specific data transit policy.
Warning noteTo ensure the correct setup of a multi-region key for use in Qlik Cloud, you must create the key-pairing according to the above backup region chart in the AWS KMS console.Qlik Cloud Government noteThe Qlik Cloud Government regions (us-gov-west-1 or us-gov-east-1) do not need a replica key configuration to register a CMK. -
Key Type—Symmetric. CMK does not support asymmetric keys.
-
Key Usage—Encrypt and Decrypt
Other settings during key creation include:
-
Entering a key alias
-
Defining the Identity and Access Management (IAM) users and roles who can administer the key
-
Selecting the IAM users and roles who can use the key in cryptographic operations
-
Configuring the key policy.
For more information about creating an AWS KMS key, see Creating keys.
Configure the AWS KMS key policy
The key policy controls access to the AWS KMS key. Each key has its own policy. The key policy must include the minimum information and permissions required to use your AWS KMS key with Qlik Cloud Customer Managed Keys. When you create a key using the AWS KMS Management Console, AWS KMS creates a default key policy with statements based on your selections during key creation. These statements determine the IAM users and roles in your account who can administer the key and use the key in cryptographic operations.
You must edit the default key policy to add the permissions and parameters required to use the key with Qlik Cloud CMK. These include:
-
Allowing Qlik's AWS proxy accounts and required IAM roles to generate a data key, encrypt, and decrypt data using your AWS KMS key. Separate IAM roles must be added to the key policy to use CMKs with Qlik Automate.
-
Identifying your Qlik Cloud TenantID. Tenant ID is used as the encryption context. AWS KMS uses the encryption context as additional authenticated data (AAD) to support authenticated encryption. This means that one tenant cannot decrypt another tenant's cipher keys. See Encryption context. If you are using the same KMS key for multiple tenants, you must include the Tenant ID for each tenant in the key policy.
Do the following:
- Make sure that your customer AWS account and IAM users and roles are correct and included in the policy, see Example AWS KMS key policy. Your policy might include other statements as well.
-
Copy the required Qlik Cloud code snippet below and add it to your key policy. For Qlik Cloud Government subscriptions, copy the Qlik Cloud Government code snippet.
-
In the EncryptionContext string, replace QLIK_TENANT_ID with your Qlik Cloud TenantID.
- Save the key policy.
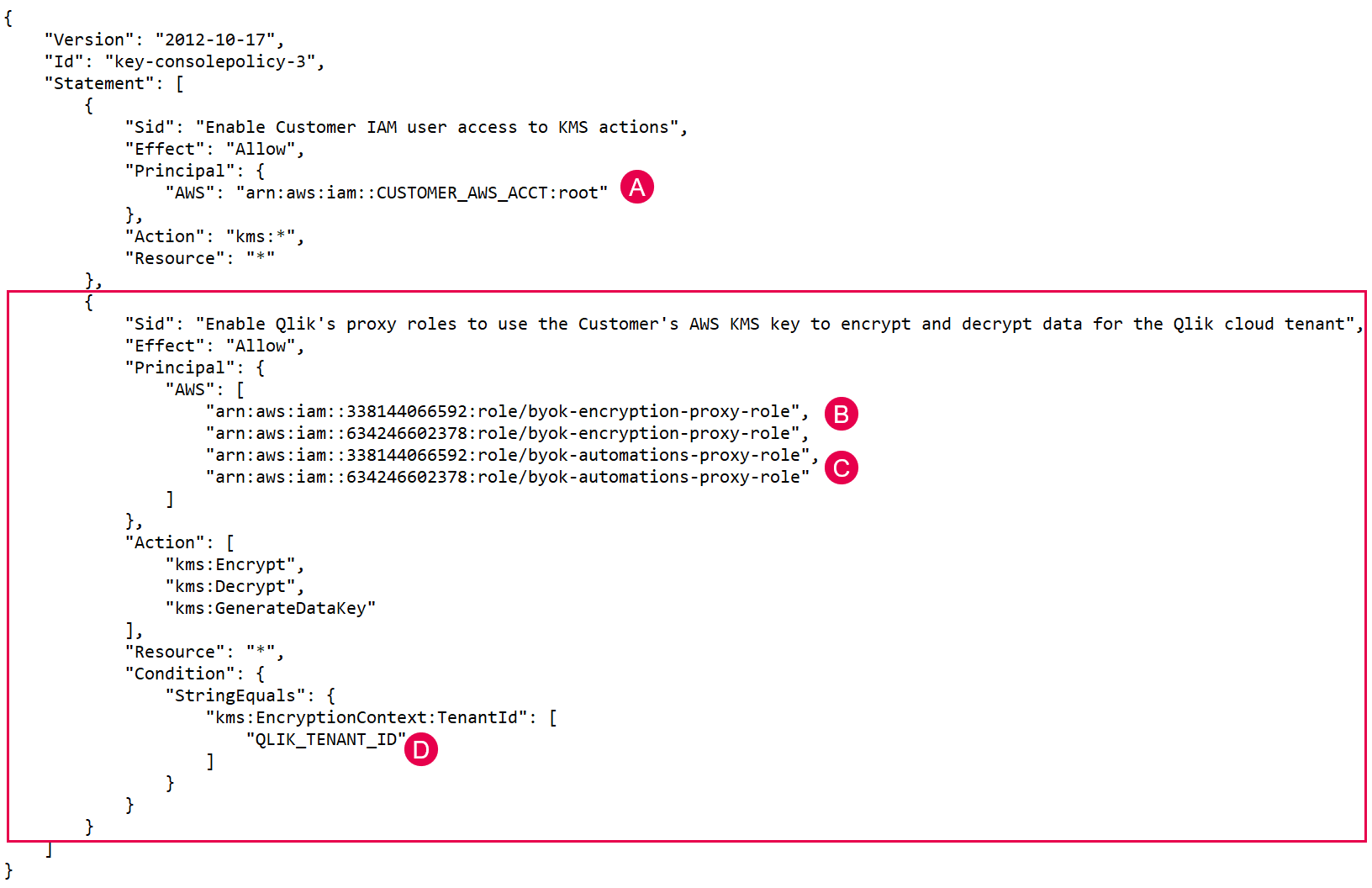
Qlik Cloud code snippet
{
"Sid": "Enable Qlik's proxy roles to use the Customer's AWS KMS key to encrypt and decrypt data for the Qlik cloud tenant",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::338144066592:role/byok-encryption-proxy-role",
"arn:aws:iam::634246602378:role/byok-encryption-proxy-role",
"arn:aws:iam::338144066592:role/byok-automations-proxy-role",
"arn:aws:iam::634246602378:role/byok-automations-proxy-role"
]
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:EncryptionContext:TenantId": [
"QLIK_TENANT_ID"
]
}
}
}Qlik Cloud Government code snippet
[
{
"Sid": "Enable Qlik's proxy roles to use the Customer's AWS KMS key to encrypt and decrypt data for the Qlik cloud tenant",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws-us-gov:iam::014729015091:role/byok-encryption-proxy-role",
"arn:aws-us-gov:iam::014734359703:role/byok-encryption-proxy-role",
"arn:aws-us-gov:iam::014729015091:role/byok-automations-proxy-role",
"arn:aws-us-gov:iam::014734359703:role/byok-automations-proxy-role"
]
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:EncryptionContext:TenantId": [
"QLIK_TENANT_ID"
]
}
}
},
{
"Sid": "Enable KMS Key policy for proxy account",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws-us-gov:iam::014729015091:role/byok-encryption-proxy-role",
"arn:aws-us-gov:iam::014734359703:role/byok-encryption-proxy-role",
"arn:aws-us-gov:iam::014729015091:role/byok-automations-proxy-role",
"arn:aws-us-gov:iam::014734359703:role/byok-automations-proxy-role"
]
},
"Action": "kms:DescribeKey",
"Resource": "*"
}
]To find your Tenant ID, from any activity center, select your user profile, and then select About. Under Tenant ID, select and copy the ID string.
Do not use the Display name or Alias hostname from the Tenant tab on the Settings page in the Administration activity center.
For more information about AWS KMS key policies, see Key policies in KMS.
Example AWS KMS key policy
The following example key policy includes the basic requirements for use with Qlik Cloud Customer Managed Keys.
-
The customer account and IAM users and roles who can administer and use the key.
-
The Qlik accounts and IAM roles that are permitted to use the key for cryptographic operations: Encrypt, Decrypt, and GenerateDataKey.
-
The Qlik accounts and Automations IAM roles that are permitted to use the key with Automations.
-
The encryption context that identifies your Qlik Cloud tenant identification number (TenantID).
The selected section (B, C, and D) in the policy example identifies the parameters required by Qlik Cloud Customer Managed Keys.
AWS KMS key policy example
KMS key ARN and alias ARN
The Amazon Resource Name (ARN) is a unique, fully qualified identifier for the KMS key. It includes the Encryption Context (TenantID), AWS account, Region, and key ID. The ARN is created when you create an AWS KMS key in the AWS Key Management Service. In Qlik Cloud, when you change the master key provider in the Administration activity center to use your AWS KMS key, you must provide the key ARN or the alias ARN to connect the Qlik encryption service to your AWS KMS key. See Create a new key provider in the tenant.
A) AWS KMS key ARN , and B) Alias ARN in the AWS Key Management Service
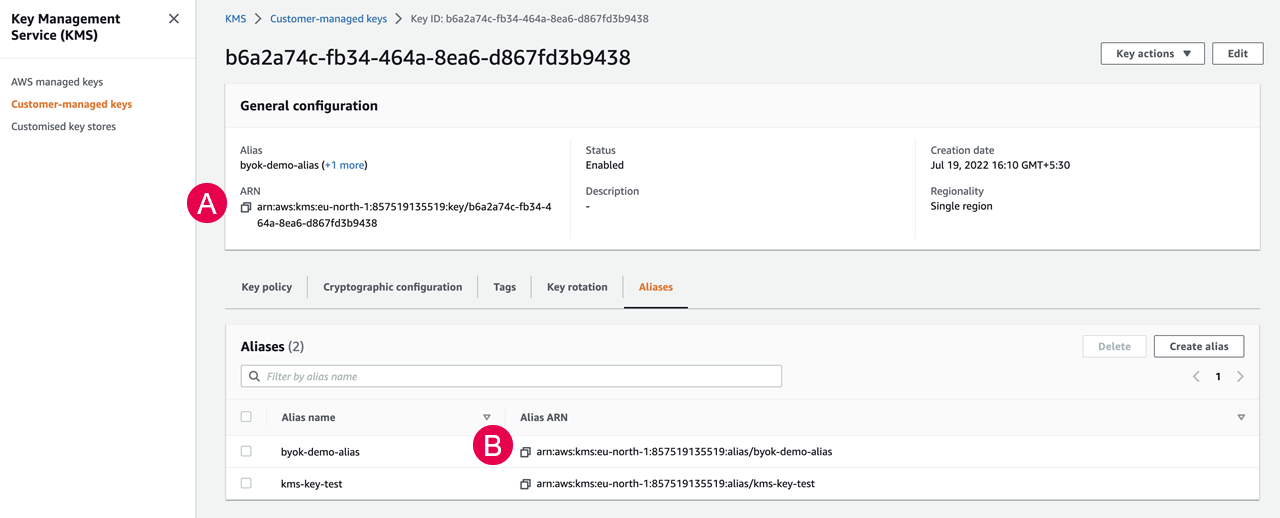
The ARN uses the format:
arn:<partition>:kms:<region>:<account-id>:key/<key-id>
The following is an example of a valid key ARN:
arn:aws:kms:us-east-1:111122223333:key/1234abcd-12ab-34cd-56ef-1234567890ab
The alias ARN uses the format:
arn:<partition>:kms:<region>:<account-id>:alias/<alias-name>
The following is an example of a valid alias ARN where CMK-Example-Alias is the alias name:
arn:aws:kms:us-east-1:111122223333:alias/CMK-Example-Alias
For more information about locating the key ARN or alias ARN for your KMS key, see Finding the key ID and key ARN or Finding the alias name and alias ARN.
AWS KMS Multi-Region Key for Disaster Recovery (DR)
Multi-region keys allow you to continue to access and process encrypted data, even when the primary region is experiencing an outage. By creating a replica of the key, you can decrypt data in the backup region, and any data encrypted in the backup can later be decrypted in the primary region once it is restored.
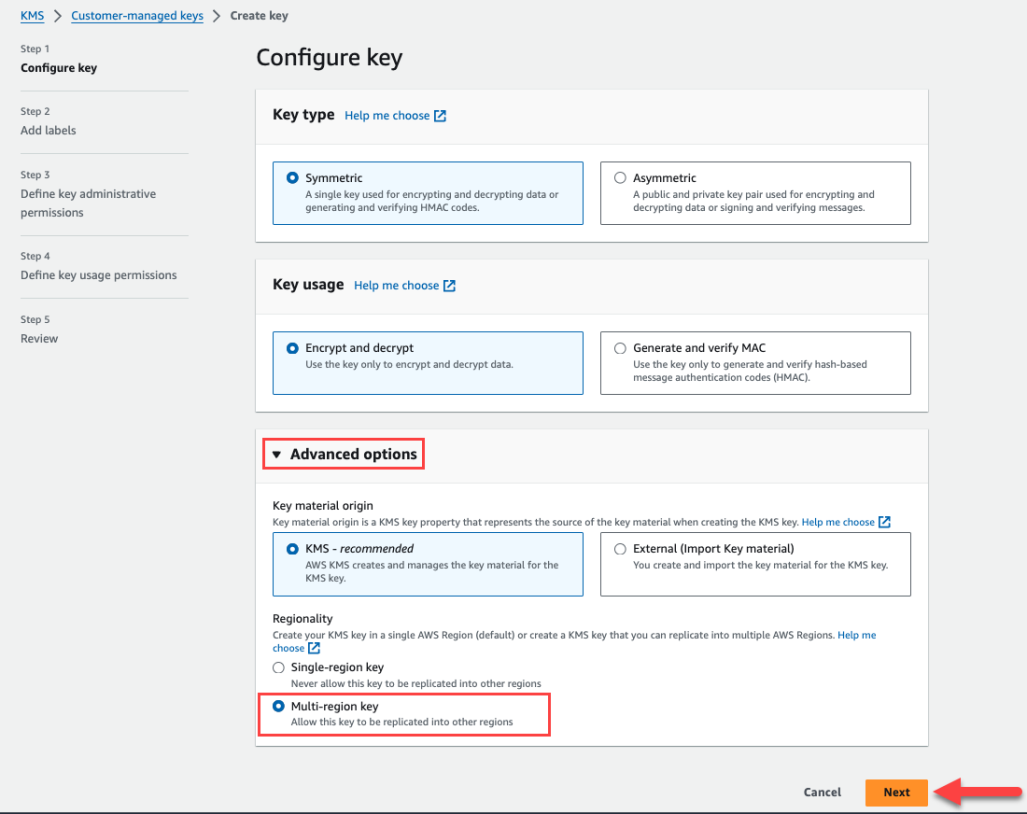
Follow these steps to create a multi-region key in AWS KMS:
-
On the AWS Management Console, click on Create a key.
-
In Step 1 you will set up your key configuration. In the Advanced options section, select KMS for the Key material origin and in the Regionality section, select Multi-region key. Click Next to continue.
-
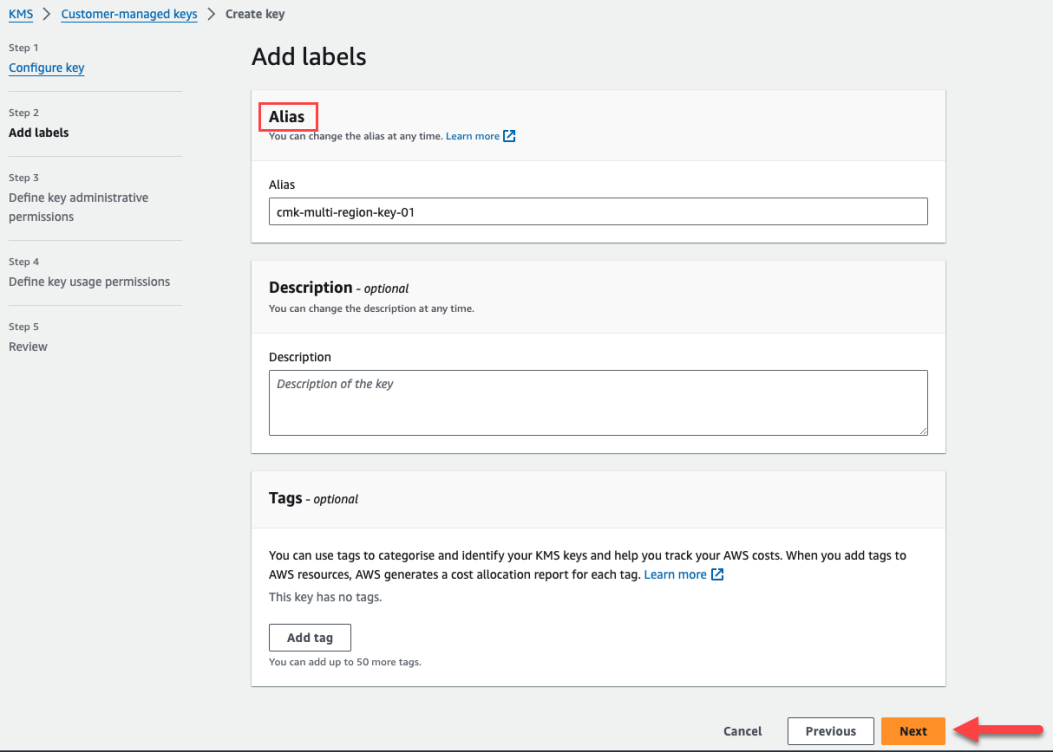
In Step 2 you will add an Alias for the key. After adding a name, you can opt to add a description and tags. Click Next to continue.
-
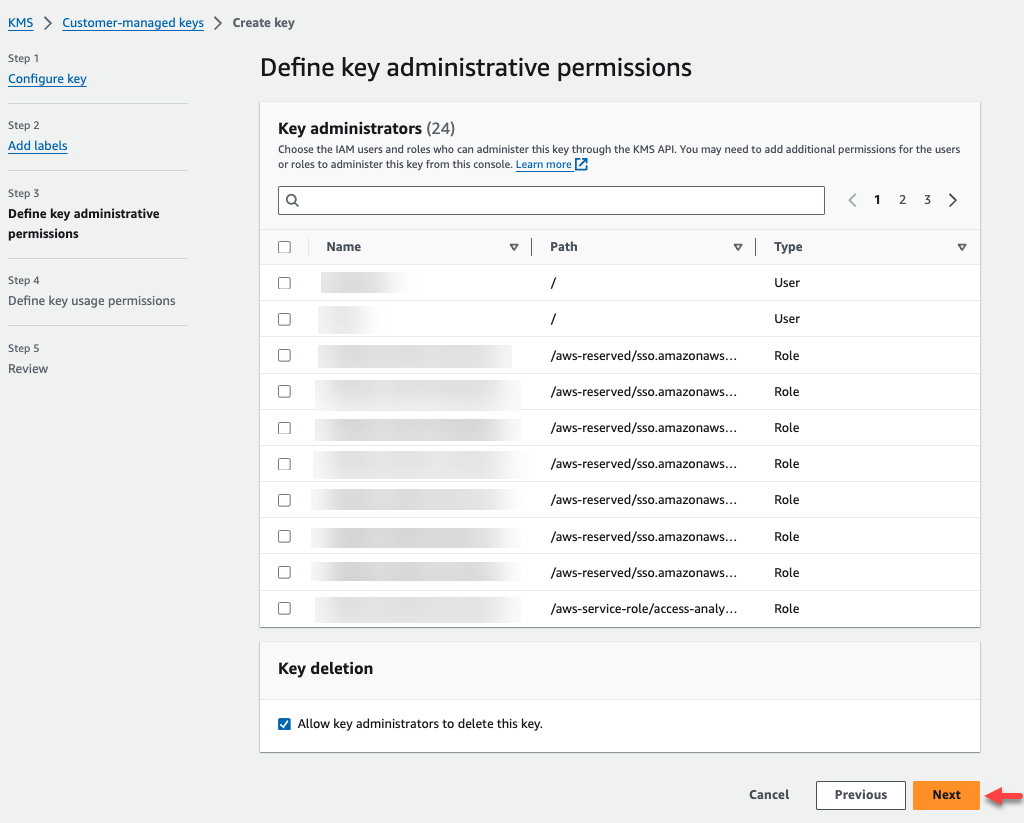
In Step 3 you can select the IAM users and roles who can administer the key. Click Next to continue.
-
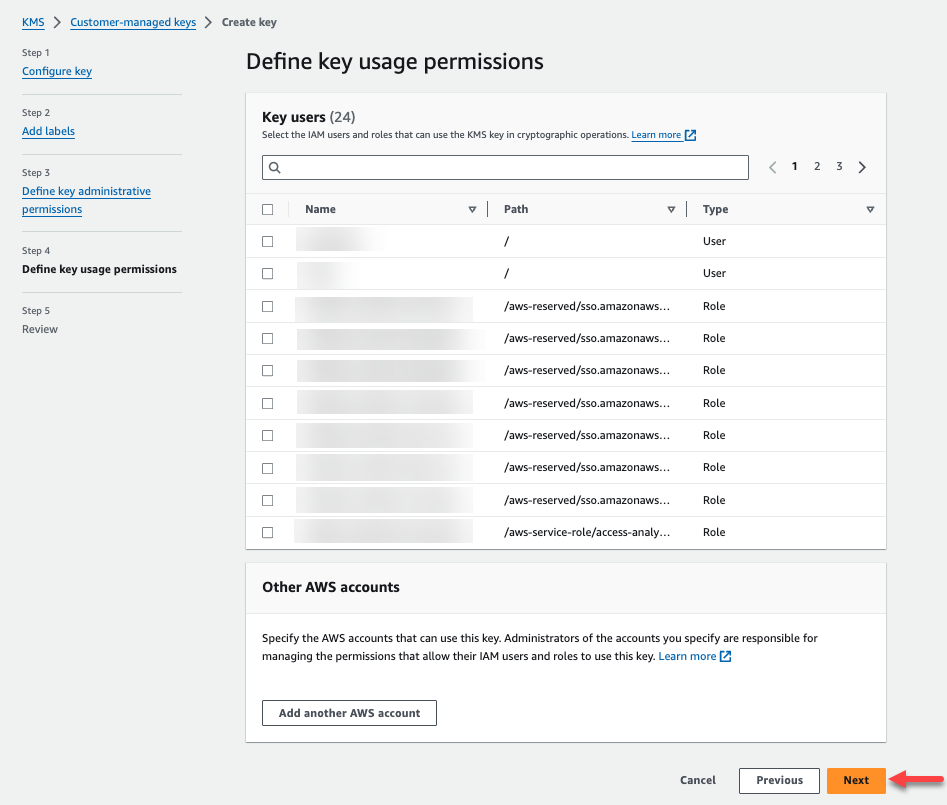
In Step 4 you can select the IAM users roles that can use the KMS key .Click Next to continue.
-
In Step 5 you will review the configuration details. Ensure that the Regionality is set to Multi-region key.
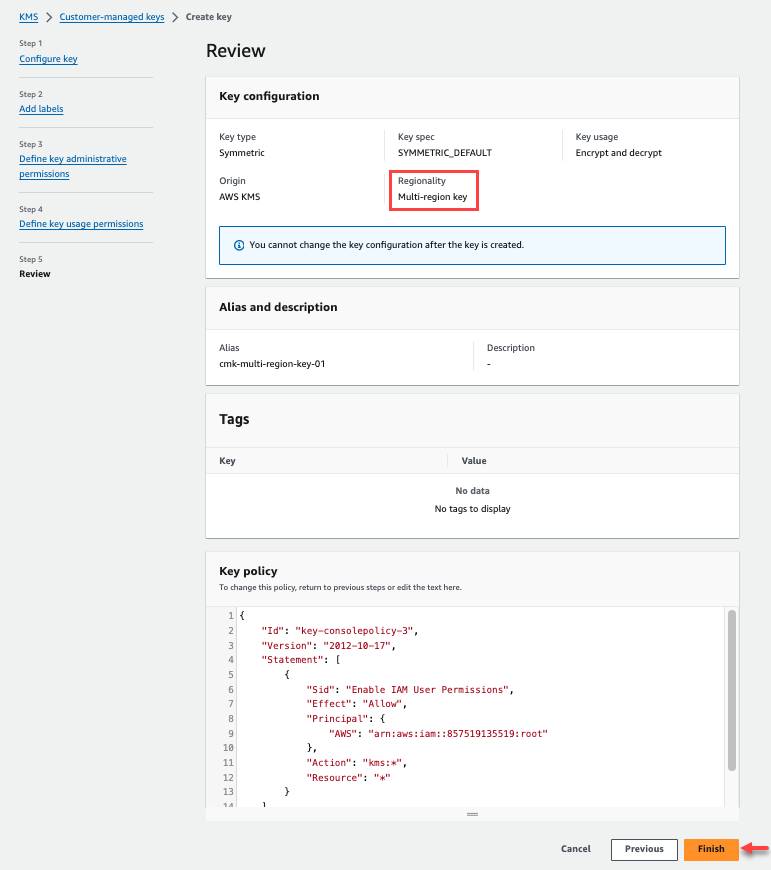
The Key policy includes all the requirements to use the multi-region key with Qlik Cloud Customer Managed Keys, including the KMS action DescribeKey. For more information about DescribeKey, please see AWS KMS DescribeKey.
