Configuring an interactive OIDC IdP
This topic describes how to configure the identity provider settings in Qlik Cloud.
Configuration on the identity provider side
In addition to the configuration in Qlik Cloud, you also need to make configurations on the identity provider side. For a walk-through of those configurations, refer to the following resources:
Configuration in Qlik Cloud
Tenant administrators can create new IdP configurations.
Do the following:
-
In the Administration activity center, go to Identity provider and click Create new.
-
For Type, select OIDC.
-
For Provider, select an identity provider from the list, or choose Generic if your specific provider is not listed.
-
Optionally, enter a description for the IdP configuration.
-
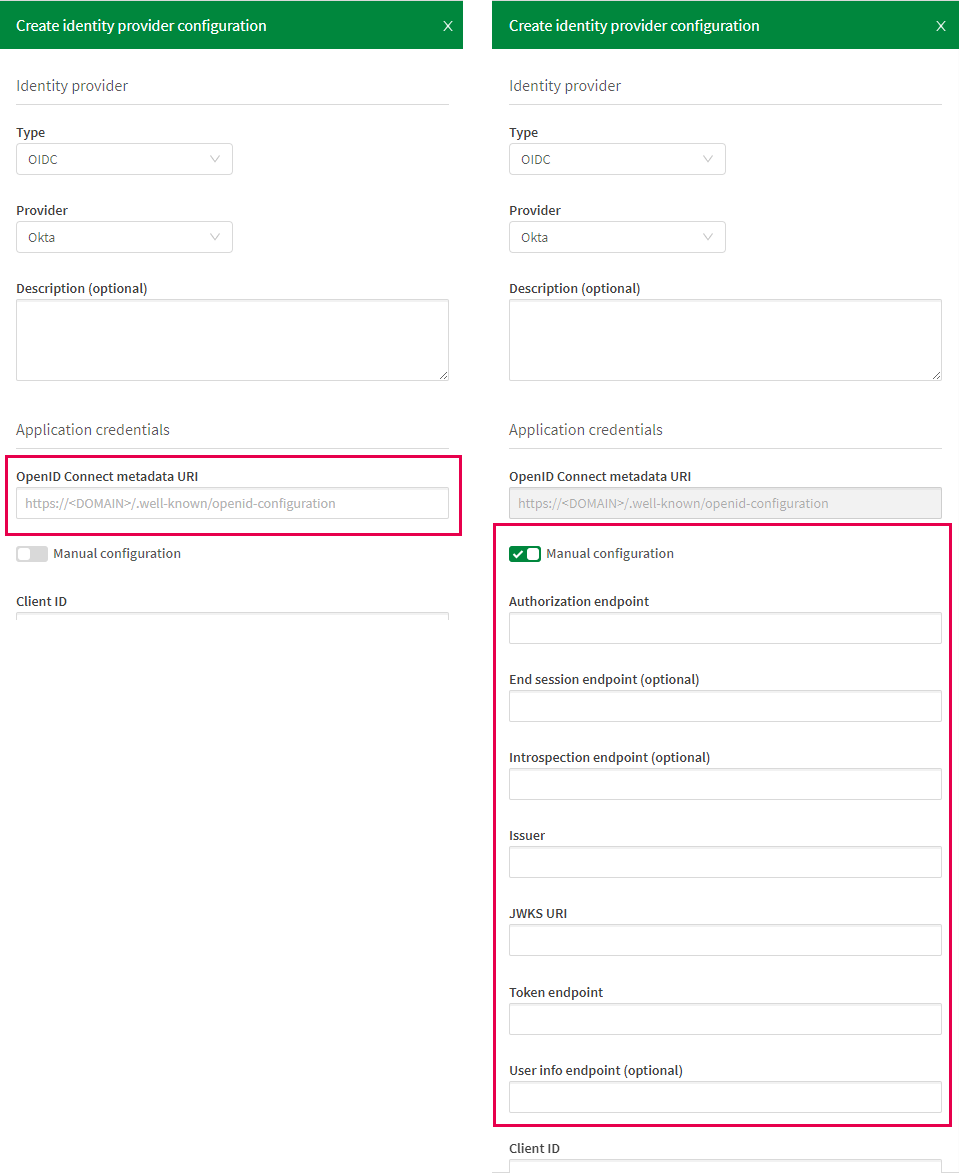
Under Application credentials, you can enter the discovery URL. If a discovery URL is not available or does not give proper metadata, you also have the option to manually enter individual values. Manual configuration should be used only when a discovery URL has not been entered.
Do one of the following:
-
Enter the discovery URL. This is the URL to the endpoint that provides configuration data for the OAuth clients to interface with the IdP using the OpenID Connect protocol. The naming conventions for the discovery URL vary based on your chosen provider:
-
ADFS: ADFS discovery URL
-
Auth0: OpenID configuration
-
Keycloak: Keycloak OpenID endpoint configuration
-
Okta or Generic IdP: OpenID Connect metadata URI
-
Salesforce: Salesforce discovery URL
-
or
-
Select Manual configuration.
-
Enter the following values:
-
Authorization endpoint: The URL for interaction with the resource owner, where you get the authorization to access the resource.
-
End session endpoint (optional): The URL used to trigger a single sign-out.
-
Introspection endpoint (optional): The URL to validate reference tokens or JWTs.
-
Issuer: The URL to the identity provider.
-
JWKS URI: The URI to the JSON Web Key Set containing public keys used for verification of a JSON Web Token (JWT).
-
Token endpoint: The URL to get an access token.
-
User info endpoint (optional): The URL to get user information.
-
Configuration using the discovery URL and manual configuration.
-
-
Enter the Client ID: The ID of the configured client at the IdP for interactive user authentication.
-
Enter the Client secret: The secret for the client configured at the IdP.
-
Optionally, enter a Realm. This is the name to associate with the IdP. It is the same as the domain name in Qlik Sense Enterprise on Windows and it is used for naming consistency in multi-cloud.
-
Fill in the fields under Claims mapping.
Claims are statements (name/value pairs) about the entity (in many cases the user) and metadata about the OpenID Connect service. Mappings are available for sub, name, groups, email, client_id, picture, and email_verified (optional).
Information note-
You can enter multiple lookup values, separated by a comma, in the input fields. The first non-null value found will be used.
-
The groups claim is needed to receive groups. Note that nested groups are not supported in Microsoft Entra ID.
-
-
Optionally, configure the advanced options. For more details, see Advanced options.
-
Click Create.
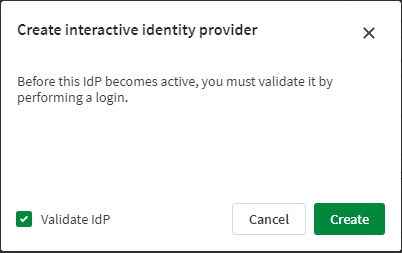
A confirmation dialog appears with the option to validate the IdP configuration.
-
To validate now, select Validate IdP and click Create. This will initiate the validation process. Follow the steps in the validation wizard to perform a login and verify that the user profile data is correct.
-
If you prefer to create the configuration now but validate it later, clear the Validate IdP checkbox and click Create. You can validate later by clicking
on your IdP configuration and selecting Validate.
Validating and creating the IdP configuration.
-
Adding your tenant URL to the identity provider allowlist
At your identity provider, add your tenant URL to the allowlist. There are different names for this setting, for example, Allowed Callback URLs, Redirect URI, or Login redirect URI.
When you add the URL, you need to append login/callback to your tenant address, as in https://<tenant name>/login/callback.
Advanced options
The advanced options provide additional capabilities for certain identity providers.
Email verified override
Enable this setting to always set the email_verified claim to 'true'. This ensures that email addresses can be used for identity mapping in ADFS and Microsoft Entra ID. It is particularly useful when switching IdPs and helps distinguish between users with identical names in the Administration activity center.
Scope
Scopes define the access privileges that are requested when issuing an access token, according to the OAuth 2.0 specification. Enter values separated by spaces to specify the permissions you want to request from the identity provider. For example, include a groups scope if the IdP requires it to support user group features.
Post logout redirect URI
Use this field to specify a URI to which users will be redirected after logging out. For detailed instructions, see Using post logout redirect URI.
Block offline_access
When using Google Identity or OneLogin as the identity provider, enable this setting to block passing the offline_access scope to the identity provider. This ensures that the configuration works correctly with Qlik Sense Mobile SaaS and OAuth 2.0 applications.
ID token signature algorithm
The RSA signature algorithm ensures the authenticity and integrity of ID tokens. Qlik Cloud supports two options:
-
RS256 (default)
-
RS512
Select algorithm based on your security needs.
Token signature verification and decryption
Generate key pairs to verify signatures and decrypt encrypted JSON Web Tokens (JWT). For detailed instructions, see Managing key pairs for signed and encrypted ID tokens (OIDC).
