Configuring SCIM provisioning in Microsoft Entra ID for Qlik Cloud
After configuring Qlik Cloud for SCIM, you must configure SCIM provisioning in Microsoft Entra ID (formerly Azure AD).
Microsoft Entra ID requirements for SCIM
-
Microsoft Entra ID with a P1 subscription or higher (formerly Microsoft Azure Active Directory P1)
-
Access to Microsoft Azure Portal and permissions to create enterprise applications for your Microsoft Entra ID.
-
Two separate applications in the enterprise application registry in your Microsoft Entra ID.
Microsoft Entra ID configuration steps for SCIM provisioning
Do the following:
-
Navigate to the Microsoft Entra ID admin center at entra.microsoft.com.
-
Go to Identity > Applications > Enterprise applications.
Alternatively, if you enter from the general Azure portal, select Enterprise applications from the Microsoft Entra ID menu.
-
Click + New application to set up the provisioning application.
-
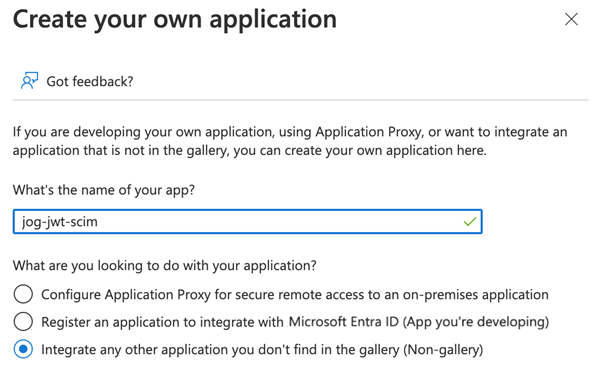
From the Browse Microsoft Entra ID Gallery page, click + Create your own application.
-
From the Create your own application dialog, enter a name for the provisioning application and select Integrate any other application you don't find in the gallery.
-
Click Create.
-
To configure the provisioning process, from the Overview page, select Provisioning from the Manage section.
-
Select Automatic from the menu. After making this selection, the configuration screens appear.
-
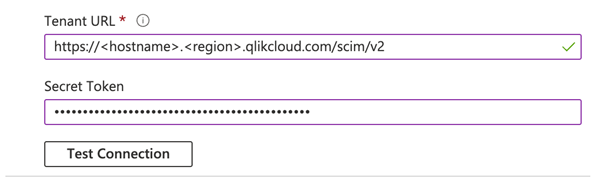
Begin the configuration by completing the Admin Credentials.
-
Paste the tenant URL obtained when you enabled auto-provisioning in Qlik Cloud.
-
Paste the token to the Secret Token box.
-
Click Test Connection.
 Information noteThe hostname is not the Qlik Cloud tenant alias. The hostname is the default name given to the Qlik Cloud tenant when it is created
Information noteThe hostname is not the Qlik Cloud tenant alias. The hostname is the default name given to the Qlik Cloud tenant when it is created -
-
Select Mappings and click Provision Microsoft Entra ID Users to configure the auto-provisioning service to work with your Qlik Cloud tenant.
-
Qlik Cloud requires a specific set of attributes to synchronize users from Microsoft Entra ID, as shown below.
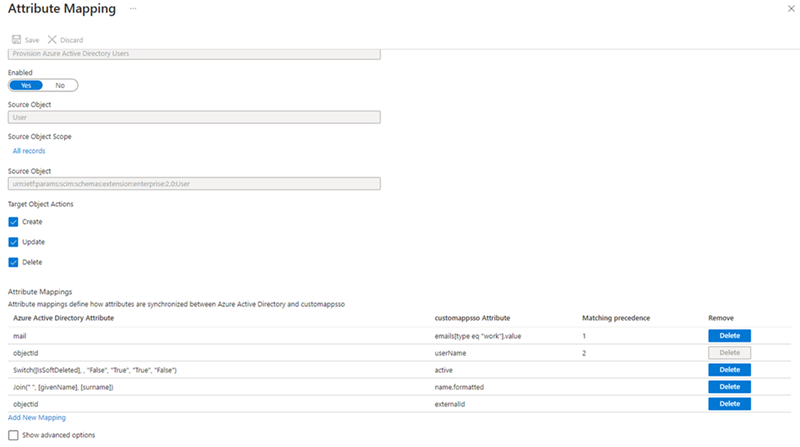
The way SCIM works between Qlik Cloud and Microsoft Entra ID is to match the user's email address (mail) first to provision and synchronize any changes associated with the user's group membership or access to Qlik Cloud.
Information noteThe UserPrincipalName attribute can be used instead of the mail attribute if the UserPrincipalName is a valid email address and is the same as the value in the email attribute sent during user authentication.The following steps configure user attribute mappings.
-
In the top section of the attribute mappings, keep all the default selections.
-
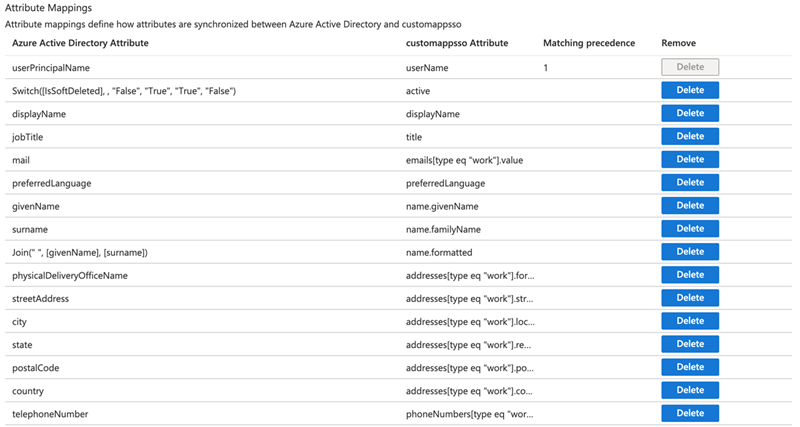
In the Attribute Mappings section, delete all the attributes except for the following:
-
userPrincipalName
-
mail
-
Switch([IsSoftDeleted], , "False", "True", "True", "False")
-
Join(" ", [givenName], [surname])
-
mailNickname
If these attributes are not deleted, the provisioning and synchronization flows between Qlik Cloud and Microsoft Entra ID will fail
-
-
Click userPrincipalName to open the attribute configuration.
-
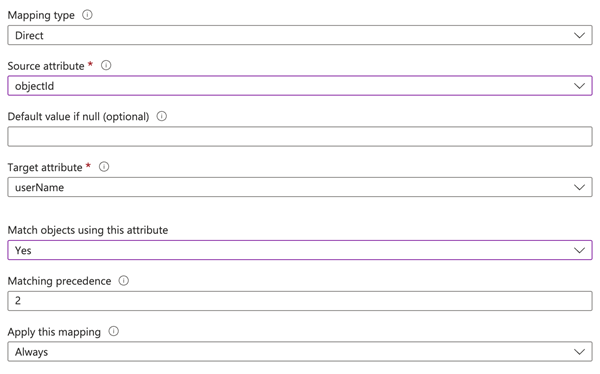
In the userPrincipalName Attribute Configuration dialog, set the Source attribute to objectId and the Matching precedence value to 2.
Click Ok to save the changes.
-
Click mail to open the Attribute Configuration dialog.
-
In the mail Attribute Configuration dialog, set the Match objects using this attribute to Yes and the Matching precedence value to 1.
Click Ok to save the changes.
-
Click mailNickname to open the attribute configuration.
-
In the mailNickname Attribute Configuration dialog, set the Source attribute to objectId.
Click Ok to save the changes.
-
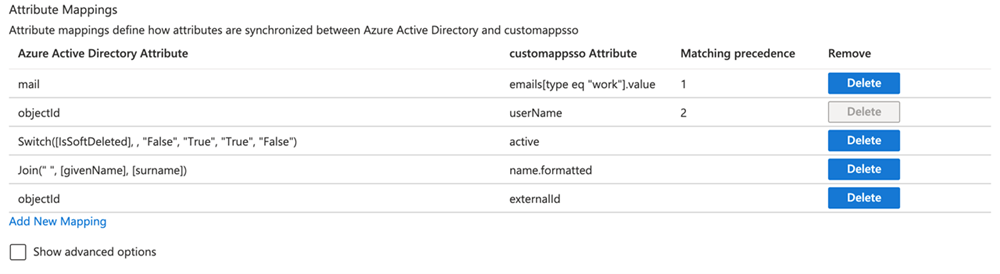
Upon completing these steps, the Attribute Mappings section looks like this.
-
Click Save at the top of the configuration page to apply the changes.
-
-
You might receive a message explaining the changes require a complete resynchronization. Assuming this is the initial configuration for SCIM with Qlik Cloud, click Yes.
The attribute mapping configuration is now complete.
-
The following steps add users and groups to provision from Microsoft Entra ID to Qlik Cloud.
-
Click Users and groups under the Manage section of the provisioning or application menus.
-
The Users and Groups table displays. Click Add user/group to add an assignment.
-
In the Add Assignment dialog, click None Selected to add users and groups.
The Users and groups dialog displays.
-
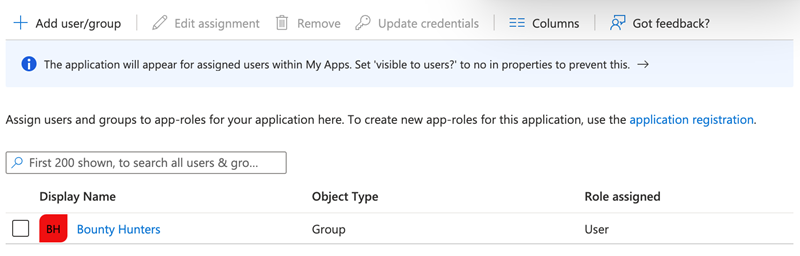
Search and add users and groups to be provisioned through this dialog. In this example, the Bounty Hunters group is selected.
Click Select to confirm the selection.
-
If you're adding a group, the Add Assignment dialog displays a warning that explains only users directly added to the group will be provisioned. Microsoft Entra ID and SCIM provisioning doesn't support cascading nested groups.
-
Click Assign to add the group to the provisioning application.
The group now displays in the Users and groups section of the provisioning application.
-
-
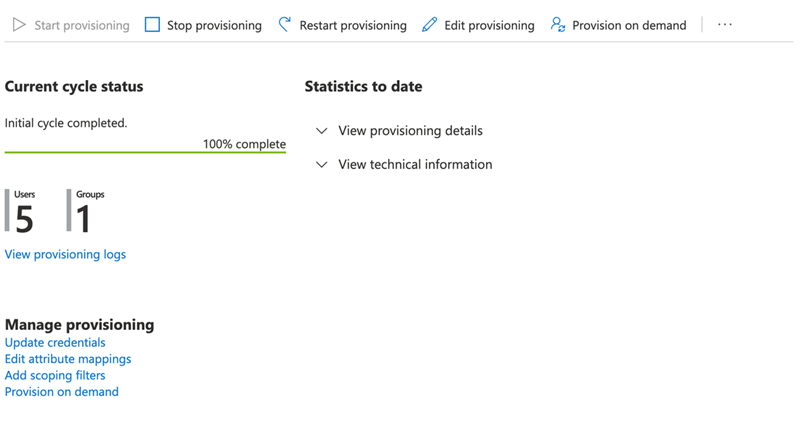
To enable auto-provisioning, go to the Overview page for the provisioning section of the application and click Start provisioning.
Information noteProvisioning might take a few minutes to several hours to complete during the first provisioning task depending on the number of users and groups being provisioned. This is a limitation of the SCIM provisioning capability. -
Refresh the page in the browser. If the provisioning process has still not run, click Provision on demand from the menu.
-
Once the provisioning process has run, the Overview page updates on a page refresh in the browser and shows the status.
-
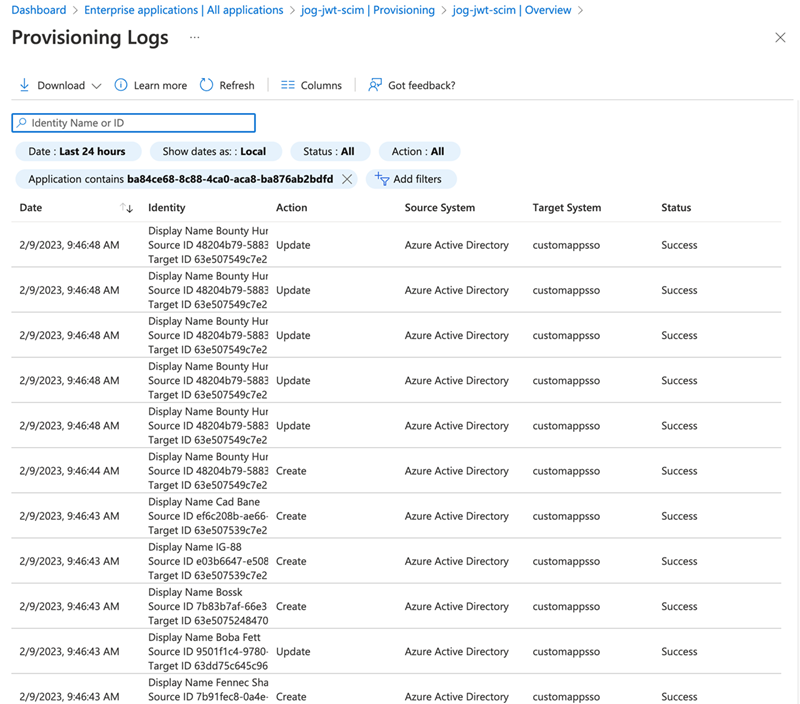
To review the synchronization, click View provisioning logs to see more detail.
Updating the SCIM token
When your SCIM token expires, you must manually renew it in Qlik Cloud. Then add the new token to your Admin Credentials of your provisioning in the Microsoft Entra admin center.
Do the following:
-
On the Overview page, click Edit provisioning.
-
In Admin Credentials, paste the new token to the Secret Token box, then click Save.
Best practices for using SCIM between Qlik Cloud and Microsoft Entra ID
-
One of the benefits of SCIM provisioning with Microsoft Entra ID is that it allows administrators to control which groups that have access to a target application, such as Qlik Cloud. It is recommended to add only the groups that represent the users and use cases you need, gradually over time. This approach makes Qlik Cloud access control easier to manage.
-
Be prepared for SCIM provisioning to take an extended amount of time to synchronize users and groups during a provisioning job. The time it takes depends on the number of users and groups you add to the application in Microsoft Entra ID.
-
If you're going to provision a large number of users to Qlik Cloud, consider adding a group to the application containing the large number of users so that you don't have to add each user to the application manually.
